I had the chance to participate with CyberErudites Team in the first edition of HackTheBox University CTF.
We ended up on TOP13. We could have done better because we were on TOP3 during the most time of the ctf… till the last 4 hours, we didn’t well managed our time ! Gg anyway guys ^_^
TOP15 will be qualified to the finals if their writeups were approved by the the organizers.
KapKan (Forensics1)
Description
Solution
We are given a zip file that contains a Microsoft Word file :
When opened :
The document contains 2 empty pages !
But wait ! What’s a docx file ?
A Docx file comprises a collection of XML files that are contained inside a ZIP archive. The contents of a new Word document can be viewed by unzipping its contents. The collection contains a list of XML files that are categorized as:
- MetaData Files — contains information about other files available in the archive
- Document — contains the actual contents of the document
Let’s unzip it then :
Let’s see the content of document.xml which contains the actual content :
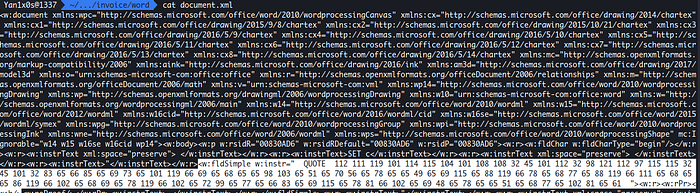
It’s an xml file but there is something weird after the section <w:fldSimple w:instr=” QUOTE.
After googling for that, we found out that it’s a method to obfuscate a payload of a macro injected inside the docx file !
Check Etienne Stalmans’s blog about MS Word Obfuscation, which is just amazing and more advanced than the basic situation we have here.
Link: https://staaldraad.github.io/2017/10/23/msword-field-codes/
Let’s de obfuscate it !
It looks like an array of integers in the range of printable ascii characters :
$ python3>>> string = “112 111 119 101 114 115 104 101 108 108 32 45 101 112 32 98 121 112 97 115 115 32 45 101 32 66 111 65 68 65 65 86 119 66 102 65 68 69 65 78 119 66 102 65 72 99 65 77 65 66 83 65 69 115 65 78 81 66>>> array = [int(x) for x in string.split(“ “) ]>>> ‘’.join( chr(x) for x in array )‘powershell -ep bypass -e SABUAEIAewBEADAAbgA3AF8ANAA1AEsAXwBNADMAXwBoADAAVwBfADEANwBfAHcAMABSAEsANQBfAE0A>>> b64command = “SABUAEIAewBEADAAbgA3AF8ANAA1AEsAXwBNADMAXwBoADAAVwBfADEANwBfAHcAMABSAEsANQBfAE0ANAA3ADMA>>> from base64 import b64decode>>> b64decode(b64command)b’H\x00T\x00B\x00{\x00D\x000\x00n\x007\x00_\x004\x005\x00K\x00_\x00M\x003\x00_\x00h\x000\x00W\x00_\x001\x0>>> b64decode(b64command).decode(‘UTF-16’)‘HTB{D0n7_45K_M3_h0W_17_w0RK5_M473}’
Explanation :
1- Convert the integers to ascii characters and concat them :
— > ‘powershell -ep bypass -e SABUAEIAewBEADAAbgA3AF8ANAA1AEsAXwBNADMAXwBoADAAVwBfADEANwBfAHcAMABSAEsANQBfAE0ANAA3ADMAfQA=’
2 — it seems like a powershell command encoded in base64.
3- decode it in utf-16 :
HTB{D0n7_45K_M3_h0W_17_w0RK5_M473}
Plug (Forensics2)
Description
We are given a zip file that contains a pcap file :
It looks like data captured from an USB device.
What kind of device is this ?
We can find that in the first frames which are sent for the exchange of the device description and configuration :
Googling for the idVendor and ifProduct, we find out that it’s a USB STICK :
Probably some file were transfered from/to this USB Stick !
We can read about the usb protocol and its filters here : https://www.wireshark.org/docs/dfref/u/usb.html
Most of the packets are under 58 bytes, except for the one that are of type URB_BULK OUT/IN !
There are interesting strings inside them and they are the ones with larger size, due to the fact that they correspond to USB messages of the type ‘bulk transfer’, used for bulk data transfers. https://geekthis.net/post/usb-sniffing-and-programming/
On the other hand, we see that this bulk data is transferred to a device with address ‘6’ in the USB bus :
So we build the following Wireshark filter to get those packets only: usb.device_address==6 && usb.capdata
More precisely, the interesting data is stored in the field ‘Leftover Capture Data’, let’s :
- extract the leftover data : tshark -r capture.pcapng -Y ‘usb.capdata and usb.device_address==6’ -T fields -e usb.capdata > raw
- convert to binary : xxd -r -p raw raw.bin
- apply file carving : binwalk raw.bin
Now that we detected that there a png file, let’s extract it using foremost :
And we got a QR code !
Let’s read it :
HTB{IN73R3S7iNG_Us8_s7UFf}
Exfil (Forensics3)
We are given a zip file that contains a pcap file :
We have some HTTP, TCP, MySQL traffic !
Following the MySQL Traffic :
We find a lot of Time Based SQL queries are invoked after some TCP traffic !
Let’s analyze those queries :
$ tshark -r capture.pcap -Y “mysql.command==3” -T fields -e mysql.query > output.txt
It’s Out Of Bound Exfiltration using time based SQL injection :
It’s leaking the value of the queried parameter BIT by BIT and doing that based on the response time : if it takes less than 3 seconds to answer then it’s a 0 else it’s a 1
In order to recover the leaked value, we need to the timestamps of each request :
$ tshark -r capture.pcap -Y “mysql.command==3” -T fields -e frame.time -e mysql.query > timed_queries.txt
Assuming that the important data is in the password column :
Let’s grep the time field only, it’s enough for our calculation :
Then, our little script will calculate the time difference between each request and determine if the bit was a 0 or a 1 :
import datetimeimport binasciitimeframe = [ int( (datetime.datetime.strptime(x.strip()[:-3], '%H:%M:%S.%f') - datetime.datetime(1900,1,1)).total_seconds() ) for x in open('time.txt').readlines() ]output = ''for i in range( len(timeframe) - 1 ) : if timeframe[i+1] - timeframe[i] < 3 : output += '0' else : output += '1'output = '0b' + output + '1'n = int(output, 2)flag = binascii.unhexlify('%x' % n)print(flag)
We run it :
My teammate KERO noticed that there is a wrong value on 2xf1l which means exfil (challenge name). we replace 2 by 3, so that it becomes 3xf1l :
HTB{b1t_sh1ft1ng_3xf1l_1s_c00l}
Warren Buffer (Forensics4)
We are given a zip file that contains a pcap file :
There is a lot of HTTPs Traffic…
Filtering out this traffic, we find some clear http traffic :
After some manual analysis and comparing different requests :
We notice that there is value that changes in the User-Agent header after the Word FourChan/XX.
Let’s grab all those values :
We got a ghostbin link : https://ghostbin.co/paste/yqtsek93
When visiting it :
We realize that it requires a password, let’s go back to the pcap and grep for password :
We are given a base64 long string, probably a file
Base64 decoding the string, we find that it’s an image from google map :
There is something odd about this image, it’s the label on the left, saying :
My bytes are washed by : 7d76830dDDBBA391F542cCbc3E598Df392a3F274
seems like a hash all the values are between 0–9 and a-f, let’s identify it :
But why is there an upper and a lower case ?
After some googling, we found this : https://ethereum.stackexchange.com/questions/2045/is-ethereum-wallet-address-case-sensitive
Thanks to HFZ !
Let’s check the transactions sent from/to our address using https://ropsten.etherscan.io :
The first one has some input data https://ropsten.etherscan.io/tx/0x14ad4152ea22032e25ae81e7538ae4257117a6b9e5954498948aab4f65a03285 :
This shows that we are on the good track !
It was sent to this address : https://ropsten.etherscan.io/address/0x0f9ede1bc4cb11e614fa739df6e303f9ab19335d
Checking the transaction before the one that had an input data ( contract creating ) :
https://ropsten.etherscan.io/tx/0x691121dbc071e3b6ffc7a33df13613fa4bee6db9de37a54a346ea57c5b64cd97
We find some input data :
After removing incorrect hex values, we get out flag :
HTB{1a4b20ec17323f20909c224614308f09}
I hope you have learnt something ^_^
Check my other writeup for a cool reverse challenge on this CTF :
https://yan1x0s.medium.com/htb-x-uni-ctf-writeup-malception-reverse-fddda3ad01e6
#Yan1x0s
